Summary
In this Hack The Box challenge, you’ll sharpen your Python skills. Your task is to write a Python script that connects to a service, extracts a specific string, calculates its MD5 hash, and sends the hash back, all within a single session and a strict time limit.
Write-Up
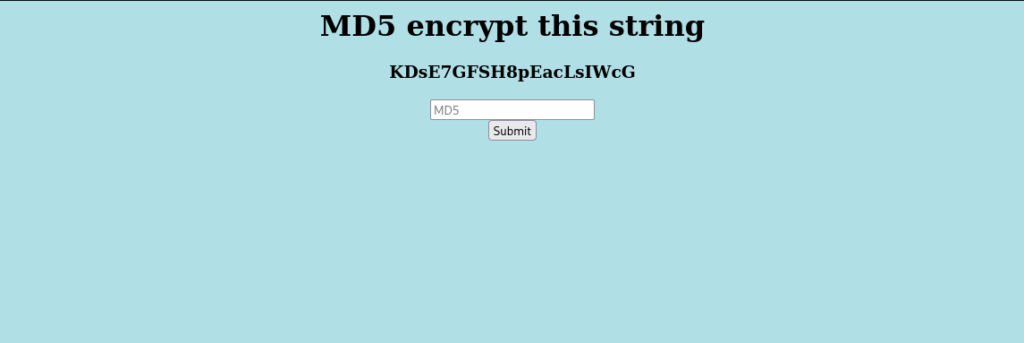
We first try to send the Md5 hash of the string back with this command
echo '<String>' | md5sum
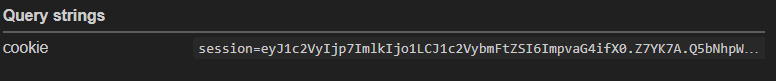
But instead we got a mocking message and another string

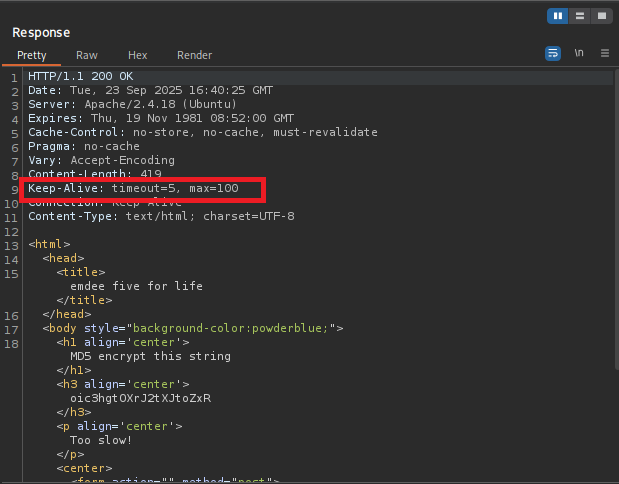
Analyze the response we can see that the website only allow us 5 seconds to get the string, hash it and send it back, all within the same session.
So I wrote this python script to get the flag:
import sys
import requests
from bs4 import BeautifulSoup
import hashlib
if len(sys.argv) <= 1:
print("Usage: " + sys.argv[0] + " http://URL")
sys.exit(1)
else:
url = sys.argv[1]
# Send the first GET request with Persistent session
session=requests.session()
response = session.get(url)
# Extract the string
soup = BeautifulSoup(response.text, "html.parser")
h3 = soup.find("h3",{"align": "center"})
# MD5 hash the string
hash=hashlib.md5((h3.get_text(strip=True)).encode()).hexdigest()
# Make the POST payload
payload = {
"hash": hash
}
# Send the payload
response2 = session.post(url, data=payload)
# Extract the Flag from the response
soup2 = BeautifulSoup(response2.text, "html.parser")
print(soup2)
flag = soup2.find("p", {"align":"center"})
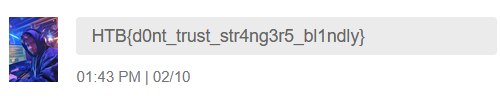
print("Flag: " + flag.get_text(strip=True))
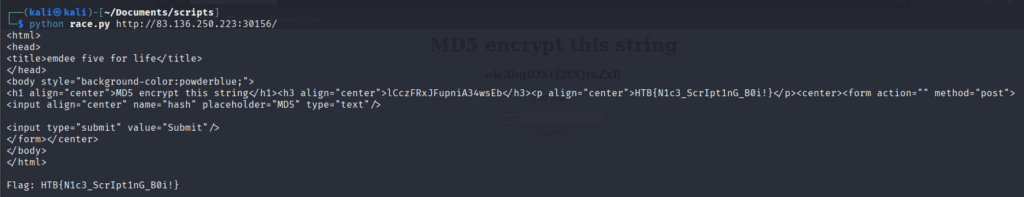
Note: there might be some delay between you and the server so run it again if it doesn’t work the first time.